- What is the LODEINFO malware?
- Analysis of LODEINFO
- Attacker infrastructure
- Summary
- IoCs
This post is also available in: 日本語
What is the LODEINFO malware?
LODEINFO is a fileless malware that has been observed in campaigns that start with spear-phishing emails since December 2019. The infection is known to occur when a user opens a malicious Word file (hereafter Maldoc) attached to the spear-phishing email. (Excel files were also abused in the early days.)
According to information released by security vendors, APT campaigns using LODEINFO target Japanese media, diplomacy, public institutions, defense industries, and think tanks. It is also suggested that the infamous APT group called APT10 is involved given the similarities in their methods and malwares.
LODEINFO malware: published information up to 2022
• APT10 HUNTER RISE ver3.0: Repel new malware LODEINFO, DOWNJPIT and LilimRAT
• APT10: Tracking down LODEINFO 2022, part I
• Unmasking MirrorFace: Operation LiberalFace targeting Japanese political entities
• Fighting to LODEINFO: Investigation for Continuous Cyberespionage Based on Open Source
• LODEINFO, a malware targeting organizations in Japan
• The evolution of LODEINFO malware
Attacks using LODEINFO have continued in 2023, with multiple versions of the malware being discovered. The malware is still being actively developed, as evidenced by the frequency of its version updates.

For information on version updates prior to September 2022, please refer to the following article:
APT10: Tracking down LODEINFO 2022, part II
We analyzed each version of the LODEINFO malware and identified changes.
Based on our analysis, the malware has been updated with new features, as well as changes to the anti-analysis (analysis avoidance) techniques and the implementation of new features. This suggests that the attackers are focusing on concealing their Tactics, Techniques, and Procedures (TTPs), including malware.
Due to the limited information on the detection, it is likely to expect that the detection of LODEINFO is becoming difficult. In 2023, only a limited number of LODEINFO samples were discovered, and the results of their investigation and analysis were not widely made public.
As of the publication of this post (January 24, 2024), we have observed a new version of LODEINFO, v0.7.3. In this article, we will detail the updates made to LODEINFO that have been observed from the end of 2022 to January 2024, including v0.7.3.
Analysis of LODEINFO
The infection flow
The following is the infection flow of LODEINFO that was observed in 2023. It shows some changes from the previous versions.
Update of the Downloader Shellcode
The initial infection path is the same as previous versions. The Infection starts from malicious Word document (Maldoc), LODEINFO is eventually injected into memory leading infection.
In 2023, the VBA code in this Maldoc was updated. Specifically, VBA code that embedded Downloader Shellcodes for both 32-bit and 64-bit was added, and the appropriate shellcode is selected depending on the target environment.
The adoption of 64-bit architecture in Windows OS is a challenge for many organizations, and LODEINFO is also likely to have changed to adapt to 64-bit architecture.

The changes in the infection flow were implemented from v0.6.8 to v0.7.1 observed in 2023 or the later versions.
Remote Template Injection
In LODEINFO v0.6.9, we have also observed more complex cases that use Remote Template Injection in the infection flow described above.
What is Remote Template Injection?
Microsoft Word has a "template" feature that allows users to create files based on templates created by other users. When a Word file that a template inserted is opened, the template is downloaded from the local or remote machine.
Using the above "template" feature, an attacker can host a Word template file (.dotm) containing malicious Macros on their server and have the malicious template be retrieved and executed from the attacker's server every time the victim opens a Word file that contains the template.
A Word file using Remote Template Injection is opened, it downloads and reads the template from the attacker's C2 server.
The downloaded template is malware that is equivalent to the Maldoc mentioned above, and it contains VBA code with the Downloader Shellcode embedded. This eventually calls the LODEINFO main body. The following is an image of the infection flow with Remote Template Injection added.
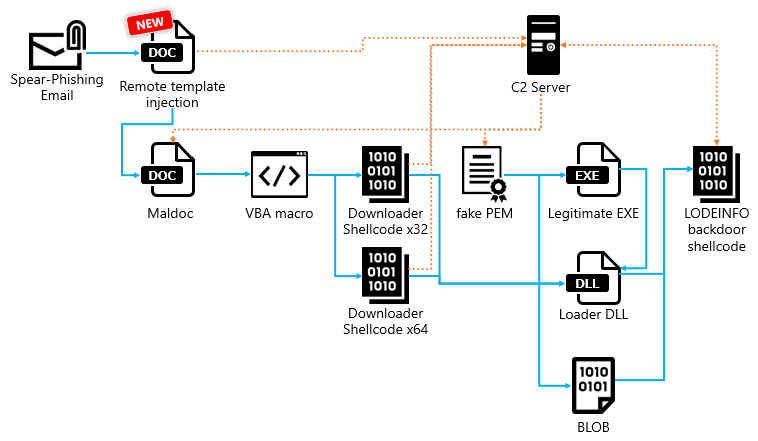
The attached Word file itself only reads the template, making it difficult to detect as malicious activity. This technique is likely intended to evade detection by security products.
To further analyze the structure of the Word file using Remote Template Injection, we can check the contents of the \word\_rels\settings.xml.rels file in the word file. This will show that the file is designed to read the template file https://45.76.222[.]130/template.dotm.

Maldoc
Next, we will introduce the VBA included in Maldoc.
VBA code embedded in Maldoc
The VBA code embedded in Maldoc contains both 64-bit and 32-bit Downloader Shellcodes.

The Macro first checks the OS architecture of the target device and then executes the Downloader Shellcode that matches that architecture.
Each Downloader Shellcode is encoded using Base64 and separated as many split parts. This is thought to be a technique to evade detection by security products.
When the Macro is executed, after the split parts are reassembled, the Shellcode decoded using Base64 is injected into memory.

Microsoft Office language check
The code to check the language settings of Microsoft Office was deployed in the v0.7.0 Maldoc. The sample we confirmed checks whether the Office setting is Japanese or not. This is thought to be created to operate only in the target language environment.

Interestingly, this feature was removed by the attacker in v0.7.1. In addition, the filename of the Maldoc itself has been changed from Japanese to English. From this, we believe that v0.7.1 was likely used to attack environments in languages other than Japanese.
The Downloader Shellcode
The Downloader Shellcode used in LODEINFO v0.7.1 is a malware that downloads and decrypts a file disguised as a PEM file (hereinafter referred to as Fake PEM) from the C2 server, and finally creates files to infect with LODEINFO.
The Shellcode itself is a very simple downloader, so we will share the analysis results of the process of decrypting data from the Fake PEM file.
What is a PEM file?
An abbreviation for Privacy Enhanced Mail file.
One of the file formats for keys and certificates used in public key infrastructure (PKI). Originally created to improve the security of email, it is now the standard for internet security.
PEM files are used in the settings of web servers, email servers, and secure communication protocols (such as HTTPS).
Fake PEM file decryption
The Downloader Shellcode downloads the Fake PEM file from the C2 server. The file is then decrypted using the following steps:
- The header and footer of the Fake PEM file are removed.
- The data from step 1 is decoded using Base64.
- The first 3 bytes of the data decoded in step 2 are removed.
- An HMAC is generated using the SHA1 hash algorithm from the password hardcoded in the Download Shellcode.
- The HMAC generated in step 4 is used as the key for AES, and the data from step 3 is decrypted using AES.
- The data decrypted in step 5 is further decoded using a single-byte XOR key.
What is HMAC (Hash-based Message Authentication Code)?
A code and technique for ensuring the integrity and authenticity of a message using a one-way hash function. It is widely used in secure communications where it is necessary to verify the sender of the data or that the data has not been tampered with in transit.
The passwords were hardcoded in the samples we investigated in the following format. If this password is not available, even if the Fake PEM file is successfully obtained, it is extremely difficult to decrypt the subsequent data.

Deployment of LODEINFO Backdoor Shellcode loaded into Memory
The data decrypted in step 6 is designed with a unique data structure. Objects such as the malicious Frau.dll are embedded in it for use in the next step. We will explain the details of the structure.

The restored data contains the following multiple objects:
Elze.exeFrau.dllElze.exe_bak
Each object is created in a file by the Downloader Shellcode and installed on the infected endpoint. Then, Elze.exe is executed. Elze.exe itself is a legitimate file, but it loads the malicious Frau.dll using DLL side-loading. Frau.dll is a very simple malware that loads the LODEINFO Backdoor Shellcode as a payload into memory.
However, in v0.6.6, v0.6.8, and v0.6.9, obfuscation is further strengthened by using Control-Flow Flattening (CFF) and Junk code. As you can see in the figure below, the left side of the program flow is very complex. The code on the right side of the figure is the part of corresponding code, but most of the code is filled with CFF (yellow) and Junk code (gray), and only a small amount of malicious code (white) is actually used. This also suggests that the attacker is focusing on obstructing analysis.

Finally, the Elze.exe_bak file, which is data with the LODEINFO Backdoor Shellcode encoded with a single-byte XOR, is read by Frau.dll and decoded as a payload.
What is Control-Flow Flattening?
A technique for making the structure of a program difficult to understand.
Simple processing is replaced with conditional branching and looping, so the processing that flows vertically in the control flow becomes arranged horizontally by conditional branching and looping. As the control flow becomes flat, the program processing flow becomes complicated and difficult to analyze.Attacking Emotet’s Control Flow Flattening – Sophos News
Similarities with the known downloader DOWNIISSA
By conducting a detailed analysis, we confirmed that the Downloader Shellcode we found and the known downloader DOWNIISSA have three similarities.
However, we believe that DOWNIISSA and the Downloader Shellcode we analyzed are from different malware families based on their structure.
Similarities:
- Self-patching mechanism to hide malicious code
- Encoding method for C2 server information
- Structure of the data decrypted from the Fake PEM file
Similarities 1: Self-patching mechanism to hide malicious code
The first similarity is the patching mechanism to decode the Shellcode itself.
DOWNIISSA, reported in 2022, had a process to patch the Shellcode itself when the Shellcode was executed. The newly found Downloader Shellcode also has a self-patching mechanism.

Although it is similar in DOWNIISA that it performs self-patching within the Shellcode, there are also clear differences. DOWNIISSA used Base64, but the current Downloader Shellcode uses XOR decoding. The XOR key is used one by one, increasing from 0x00 to 0xFF.
Similarities 2: Encoding method for the C2 server information
The second similarity is that the encoding method of the C2 server information embedded in the Shellcode is the same. The Downloader Shellcode contains two C2 server addresses, which are encoded with a single-byte XOR. The embedding method is also very similar, not only the encoding method.

Similarities 3: Structure of the data decrypted from the Fake PEM file
As mentioned above, the structure of the data decrypted from the Fake PEM file is a unique structure, and it has been confirmed that it adopts the same data structure as which decrypted by DOWNIISA.
LODEINFO Backdoor Shellcode
LODEINFO Backdoor Shellcode is a fileless malware that allows attackers to remotely access and operate infected hosts. The following features were the same as the published information.
- The C2 server address uses a unique data structure.
- A mechanism that refers to the address of the embedded data is characteristic.
- The Backdoor Command ID is hidden using 2-bytes XOR.
- The structure and encryption of the communication data with the C2 server are very complex, as shown in the figure below.
- The above encryption uses the Vigenere cipher multiple times.
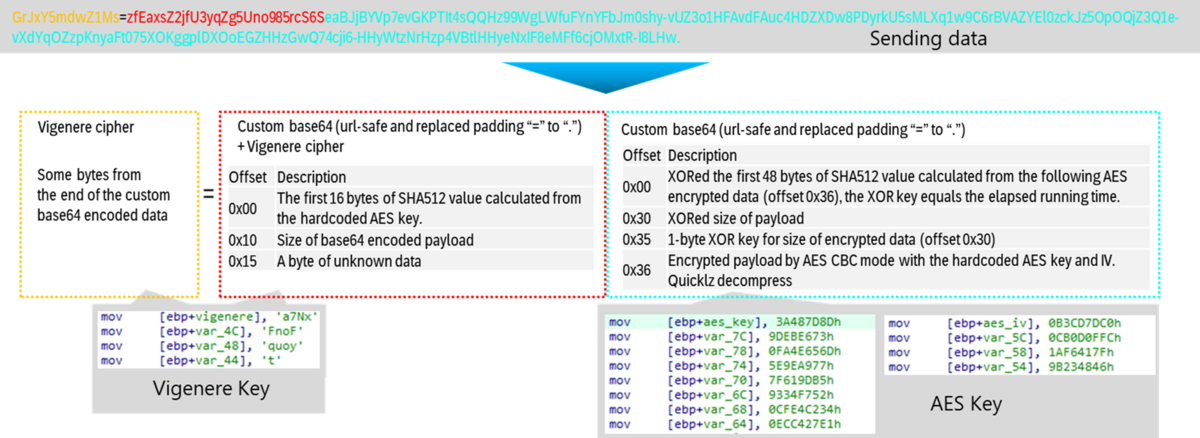
Our analysis of multiple LODEINFO samples found in 2023 revealed the following differences from previously published information:
- Change in the hash calculation algorithm for obtaining API function names
- Addition of backdoor commands
Change 1: Change in the hash calculation algorithm for obtaining API function names
The v0.7.0 version uses a new hash calculation algorithm compared to v0.6.9. This change makes it impossible to match signatures using the same rules as previous samples.
The hash calculation algorithm is used by malware to calculate the hash of API function names and resolve function addresses. The hash calculation logic includes a hard-coded XOR key that is different for each sample. This key is used for XOR decoding, so the hash values embedded in each sample are different.

Change 2: Additions to backdoor commands
LODEINFO implements the following backdoor commands to control infected hosts:
The number of backdoor commands was reduced to 11 in v0.6.5, but v0.7.1 restored 6 commands and added the new runas command, bringing the total to 18.
Additionally, four commands (keylog, ps, pkill, autorun) that were removed in v0.7.2 and v0.7.3 have been restored.
Furthermore, the content of the config command, which previously displayed "Not Available," has also been implemented.
| Command | Descriptions | v0.6.5 | v0.7.1 | v0.7.2, v0.7.3 |
|---|---|---|---|---|
| command | List the embedded backdoor commands. | Enable | Enable | Enable |
| ls | Get a list of files. | Removed | Enable | Enable |
| rm | Delete a file. | Removed | Enable | Enable |
| mv | Move a file. | Removed | Enable | Enable |
| cp | Copy a file. | Removed | Enable | Enable |
| cat | Upload a file to C2. | Removed | Enable | Enable |
| mkdir | Create a directory. | Removed | Enable | Enable |
| send | Download a file from C2. | Enable | Enable | Enable |
| recv | Upload a file to C2. | Enable | Enable | Enable |
| memory | Inject Shellcode into memory. | Enable | Enable | Enable |
| kill | Kill a process by process ID. | Enable | Enable | Enable |
| cd | Change directory. | Enable | Enable | Enable |
| ver | Send malware and system information. This includes the current OS version, malware version, process ID, path of the executable file, system username, current directory, C2 and Mutec names. | Enable | Enable | Enable |
| Take a screenshot of the desktop. | Enable | Enable | Enable | |
| ransom | Encrypt files using a generated AES key, and simultaneously encrypt that AES key using a hardcoded RSA key. | Enable | Enable | Enable |
| comc | Execute a command using WMI. | Enable | Enable | Enable |
| config | Write settings to the registry (implemented in v0.7.2, this function only returned "Not Available." prior to v0.7.1). | Not Available | Not Available | Enable |
| runas | Run a command as a specific user (implemented in v0.7.1). | N/A | Enable | Enable |
| keylog | Save the keystrokes, date and time, and name of the active window from the suspect endpoint. Use single-byte XOR encryption, and the file is saved to %temp%%hostname%.tmp. | Removed | Removed | Enable |
| ps | List processes. | Removed | Removed | Enable |
| pkill | Kill a process. | Removed | Removed | Enable |
| autorun | Set and remove persistence. | Removed | Removed | Enable |
Attacker infrastructure
Based on the analysis results of LODEINFO presented so far, we will introduce the characteristics of the communication destinations obtained from each sample.
The trend of the attacker's infrastructure that we observed in 2023 is consistent across versions, and the trend of attackers preferring to use AS-CHOOPA continues.

Summary
In 2023, multiple versions of LODEINFO were also observed, and v0.7.3 was observed in January 2024. It is important to continue to be careful, as there is a high possibility that various new features and detection evasion techniques will be incorporated in the future.
As a countermeasure, since both the Downloader Shellcode and the Backdoor Shellcode of LODEINFO are fileless malware, it is essential to introduce a product that can scan and detect malware in memory in order to detect it. Based on our research results to date, we are not only introducing products that can scan in memory, but we are also taking various measures that are specialized for LODEINFO. We will continue to expand our research and countermeasures in the future.
We hope to continue to exchange information on the threat of LODEINFO with the CERTs in organizations that are exposed to the cybersecurity threat and need the analysis.
Finally, two presentations on LODEINFO are scheduled for JSAC2024.
Although the application for participation has ended, some materials will be released later, so please use them to obtain the latest information.
IoCs
MD5 of samples:
69dd7fd355d79db0325816569ae2129a - Maldoc
E82d98bae599cd172bb194adbdc76873 – zip file of above Maldoc
D1a925ddb6d0defc94afb5996ed148bd - Maldoc
9598b2af9dd1493dd213dbca56912af4 - Maldoc
2a9012499d15145b5f63700c05adc426 - Loader module
508aed3687c146c68ad16326568431ab - Loader module
60dea5b5f889f37f5a9196e040bce0eb – BLOB:encrypted LODEINFO v0.6.9
3d910e8ab29362ae36de73c6b70a7e09 – BLOB:encrypted LODEINFO v0.7.1
290c5f33a4f4735e386b8193b1abdcf9 – Artifact:unique data structure for malware set
C2s:
167.179.106[.]224
167.179.77[.]72
172.104.112[.]218
202.182.116[.]25
45.76.197[.]236
45.76.222[.]130
45.77.183[.]161